Understanding the M365 Shared Responsibility Model: Do You Need a Third Party to Back up Your Data?

Millions of users rely on Microsoft 365 apps like Outlook, Teams, SharePoint, and Word. These apps help people work, collaborate, and communicate, whether they run a small business or a large enterprise.
But what would happen if you lost your M365 data and configurations? Many businesses aren’t familiar with the M365 security business model, and wrongly assume that Microsoft backs up their M365 apps for them. This is not true. If you don’t have extra security measures, you could lose your M365 data and configurations entirely in an outage.
In this blog, we will explain the shared responsibility model and give you an M365 security checklist to help you protect your organization and reduce the risk of loss to your Microsoft 365 environment.
The M365 Shared Responsibility Model: Who Owns What?
Microsoft 365 services, like many other “as a Service” products, follow a shared responsibility model which outlines what Microsoft is responsible for and what the user is responsible for. Many M365 users are not aware of their responsibilities and their organizations are left exposed to various risks like data loss, downtime, breaches, or accidents.
A helpful way to simplify the shared responsibility model is to remember the days of DIY “kit” homes. For these “do it yourself” kit homes, you could order the materials and the blueprint to build an entire house from a vendor. Then, it was your responsibility to build the house securely to code, maintain it, and protect it.
To fully explain M365 security best practices, we’ll cover each side of the shared cloud responsibility model:
In M365, Microsoft is responsible for:
- The uptime and availability of your applications within the M365 suite (not the information stored within them)
- Data replication within the M365 suite (meaning your M365 data is dispersed across geographic locations)
- Providing M365 access controls (but not access configuration or the implementation of access controls)
- Restricted physical access (meaning unauthorized users cannot get into Microsoft’s physical server locations)
In M365, the user is responsible for:
- Regulatory compliance obligations: It’s up to your organization to apply device control best practices based on real-time feedback of the environment. This includes weeding out false positives, making sure everything is operating as it should, and if there is a threat – taking action.
- M365 data retention/restoration: If you have business critical M365 applications (think SharePoint, Outlook, Teams), you’re responsible for the data that lies within these apps. Can your business manage without this data? Probably not. It’s up to your organization to arrange a third-party backup plan to make sure this data is secure and readily available to restore in the event of an outage.
- Tenant configuration & restoration: It is the user’s responsibility to actively validate, protect, and monitor the configuration of their tenant. Failure to do so can impact the entire M365 application set.
- Access control configuration and implementation: Your organization is responsible for your own identity and access management. This includes your identity infrastructure (particularly Active Directory), configurations, monitoring alerts, reviewing configuration changes, and ensuring you’re using the most recent best practices.
Many users don’t realize how much responsibility they carry when using M365 apps. You should always back up your data and configurations securely as part of your business continuity plan, so you can be prepared in case of an outage.
Next Steps: Protect Your M365 Data with SafeGuard365
Your M365 data and configurations face countless risks in today’s hybrid setting. Your business needs extra protection to make sure you can always restore them.
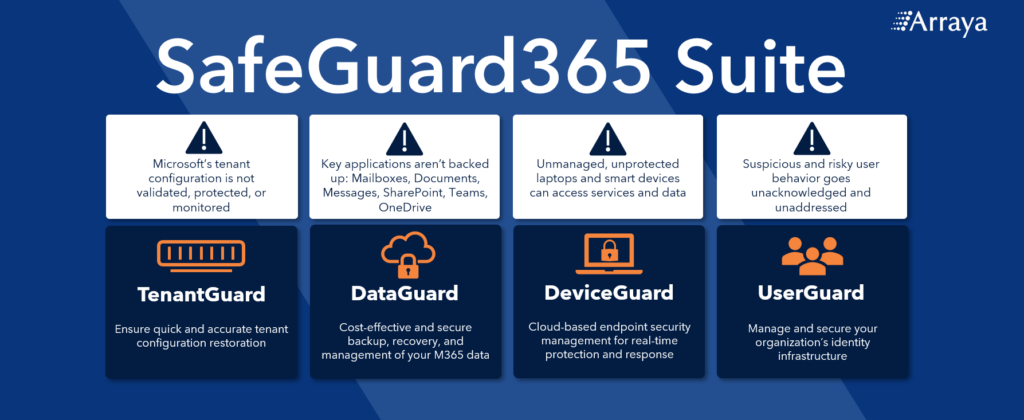
Arraya’s SafeGuard365 Suite provides cloud-to-cloud backup and recovery with comprehensive loss protection that’s unmatched across four individual M365 security products, including:
- TenantGuard: Proactively ensure your tenant is safely configured with industry-specific standards and easily recoverable in the event of an incident.
- DataGuard: Cost-effective and secure backup, recovery, and management of your M365 data.
- DeviceGuard: Comprehensive cloud-based endpoint security management for real-time protection, threat detection, and response for devices accessing M365.
- UserGuard: Integrate Microsoft Defender for Identity to secure your organization’s identity infrastructure, particularly Active Directory, to detect threats and optimize identity configurations.
This affordable suite of managed services offers a simple and economical way to eliminate these vulnerabilities. This solution is designed to optimize your IT investment and significantly reduce overhead costs.
Get in touch with us today to schedule a no-obligation M365 security assessment.

Michael Piekarski
Michael Piekarski is the Cybersecurity Practice Director for Arraya Solutions. With over 18 years of experience in Security and IT, Michael began with a robust engineering background in systems, network, and cloud engineering. In 2011, he transitioned to penetration testing and cybersecurity consulting, performing offensive security testing while also working in automation, DevOps, and SIEM deployments. Since 2019, Michael has been leading the cybersecurity practice at Arraya Solutions, leveraging his extensive expertise to provide strategic advisory roles for numerous clients.