Azure AD MFA Enhancements Begin in February 2023: Plan Your Transition
Multi-factor authentication has become a de facto technology for enhancing security for all types of applications from online apps to desktop apps to VPNs. We’ve all experienced receiving phone calls, text messages, and notifications after providing a username and password.
However, the experience of MFA within the Microsoft Authenticator app has been limited for Microsoft 365 users as compared to Microsoft Live account holders.
To address this discrepancy, Microsoft has announced the general availability of several security enhancements for Microsoft 365 users within the Microsoft Authenticator app.
The History of MFA Fatigue Attacks, Microsoft Live & Number Matching
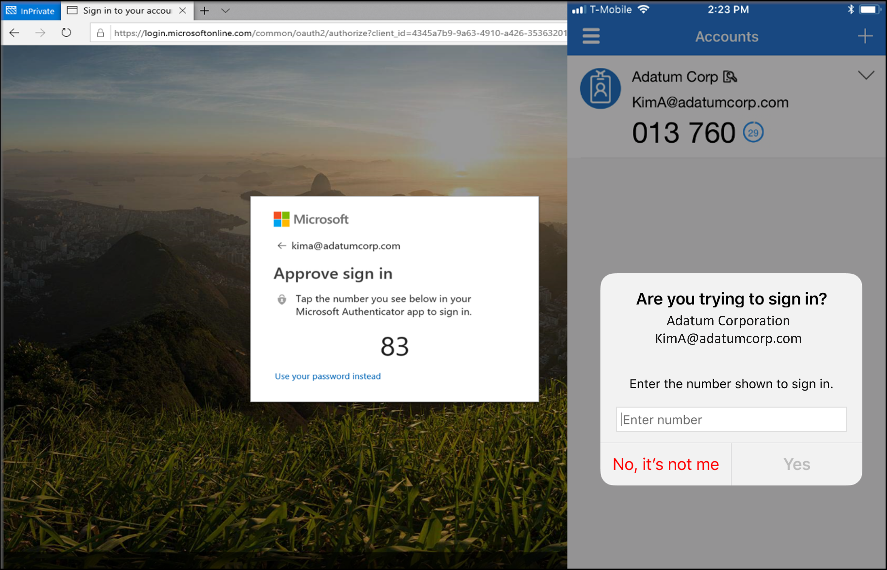
Previously, Microsoft Live was susceptible to an attack called “MFA fatigue” in which users would only receive “Accept” or “Deny” prompts if they used the Microsoft Authenticator app.
MFA fatigue attacks involve an attacker who can correctly guess a user’s credentials by constantly pushing MFA prompts until the user gets to a point where they will hit “Accept” just to stop the prompts. MFA fatigue attacks have ramped up in frequency ever since the pandemic and have affected major corporations.
To address this vulnerability, Microsoft Live account users have previously utilized a feature called Microsoft Authenticator number matching for MFA. This verification method requires that the user choose the matching number seen on the sign-in screen within the notification.
We have heard from multiple Microsoft 365 customers that they wished this feature was available for their users. Fortunately, Microsoft has now provided general availability for companies to implement these enhancements to Azure AD security. This isn’t limited to just Azure number matching but also geo-location verification!
Azure MFA Authentication Methods: Number Matching & Geo-Location Verification
Geo-location verification will elevate a user’s awareness of whether their Microsoft 365 identities are under siege. With Geo-location verification, the MFA prompt includes a prompt to enter a number and show a digital map of their approximate location based on the public IP address.
“This feature is a key security upgrade to traditional second factor authentications.” – Microsoft
Typically, only Azure AD administrator roles were able to see geographic details for user access and user sign-in. Although this was helpful, it didn’t necessarily help users take proactive measures themselves. Further, admins may not always monitor sign-in logs to catch these attempts.
Now, users will be able to report these rogue sign-in attempts, MFA requests, and social engineering in general so their administrators can block the locations found with the appropriate access controls.
Next Steps: How to Implement These Features into Your Policy
Come February 27th, 2023, Azure AD multi-factor authentication and number matching will be enabled by default for all Azure tenants. This means that users who have the MS Authenticator app as their default authentication method will be forced to utilize number matching for MFA prompts.
To avoid unnecessary calls to your help desk, it’s best to get ahead of this transition. Number matching can be configured today in a phased approach using security group assignments and internal communications. Configurations can be done using the Azure Portal or Microsoft Graph.
There are also additional configurations to keep in mind if you utilize Azure AD MFA for ADFS or NPS. Users that do not use the Authenticator app will not see this change.
To learn more about the enablement of this feature, contact your Arraya account executive today.
Visit https://www.arrayasolutions.com//contact-us/ to connect with our team now.
Comment on this and all of our posts on: LinkedIn, Twitter and Facebook.
Follow us to stay up to date on our industry insights and unique IT learning opportunities.

