How to Eliminate QuickTime Threats Using Microsoft SCCM
Earlier this week, TrendMicro posted a blog informing the public of two major vulnerabilities it found within Apple QuickTime software. Apple is no longer issuing security updates for QuickTime so the only way to be completely safe is to uninstall it from your machine. For organizations with hundreds or thousands of workstations, this could be a nightmare to deal with and an easy entry point for hackers.
The question is, what can IT do about it?
Microsoft’s System Center Configuration Manager (SCCM) can help organizations protect themselves from this threat by identifying all assets with QuickTime installed and then subsequently removing the software. There are a number of ways you could accomplish this with SCCM. Here is an example of one way you might go about it.
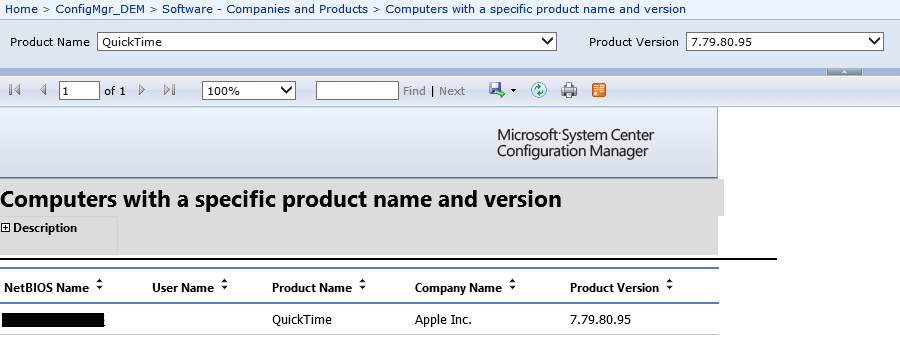
The first step is to identify the attack footprint for your organization by identifying the computers that have QuickTime installed. SCCM has simple, built-in reporting around the information it gathers from the computers in the organization. The report you are looking for is under Software – Companies and Products – Computers with a specific product name and version.
In the Product Name field, just type QuickTime and select the Product version. In Arraya’s demo environment, we didn’t have any computers with QuickTime except one (see below). This report gives you a good idea of the challenge ahead of you and the potential impact.
The second step is to start removing the software and provide protection against computers that may have it installed in the future. This kind of automation can be done by using what is known as Configuration Baselines. These will automatically populate a target list for the uninstall command.
In order to remove the software, we have to find it first. There are a number of ways this can be accomplished, including looking for related files and folders. In this example, we will detect the uninstall registry key for the software. This is a very strong method to detect any software that is listed in Add/Remove Programs. Start by opening up the SCCM console and creating a new Configuration Item called “Detect QuickTime.”
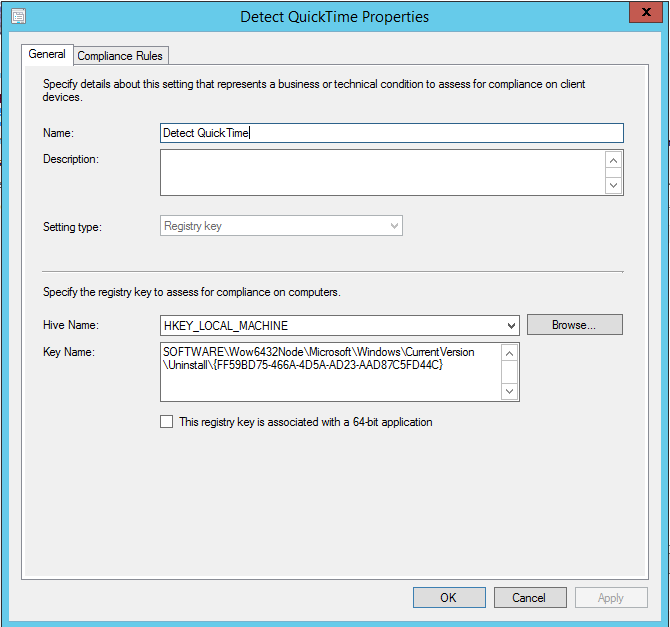
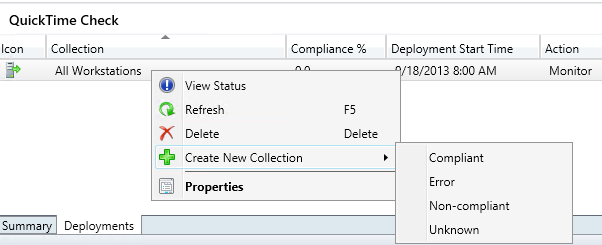
Instruct this configuration item to consider any computers with this key to be Non-Compliant. This can be deployed to all systems or all workstations in the environment. It will instruct each machine to check for the existence of this particular registry key. When detected, the machine will report back to SCCM that it is not compliant. From here, we can build a group of computers known as a Collection. This can be built automatically based on the computers reporting Non-Compliance.
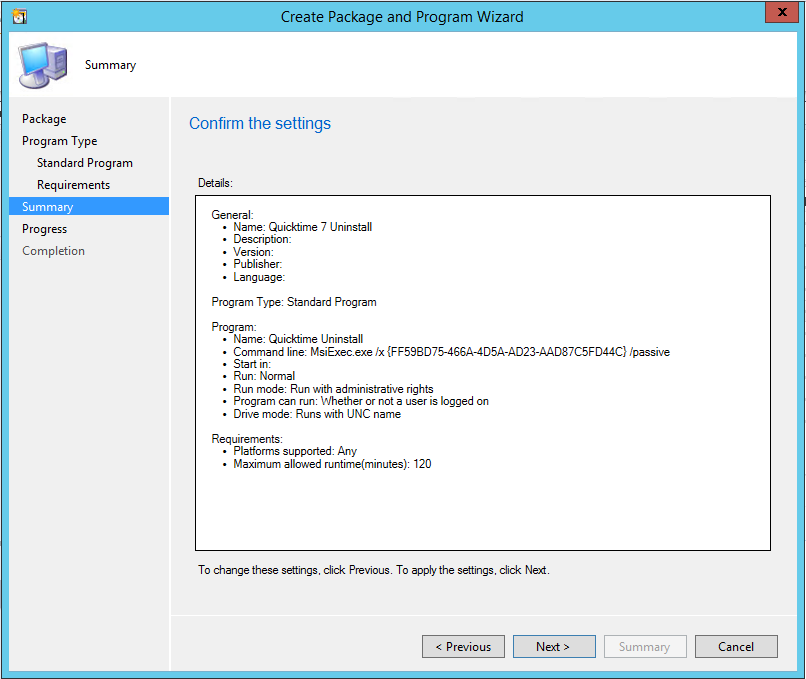
The populated Collection of computers is where you deploy the uninstall command. In this case, we use a simple package to deliver the command. The command to uninstall QuickTime is:
MsiExec.exe /x {FF59BD75-466A-4D5A-AD23-AAD87C5FD44C} /passive
Back over to our test computer that has QuickTime, you can look at the status of the Baseline we just created. You can see that this computer is now considered Non-Compliant.
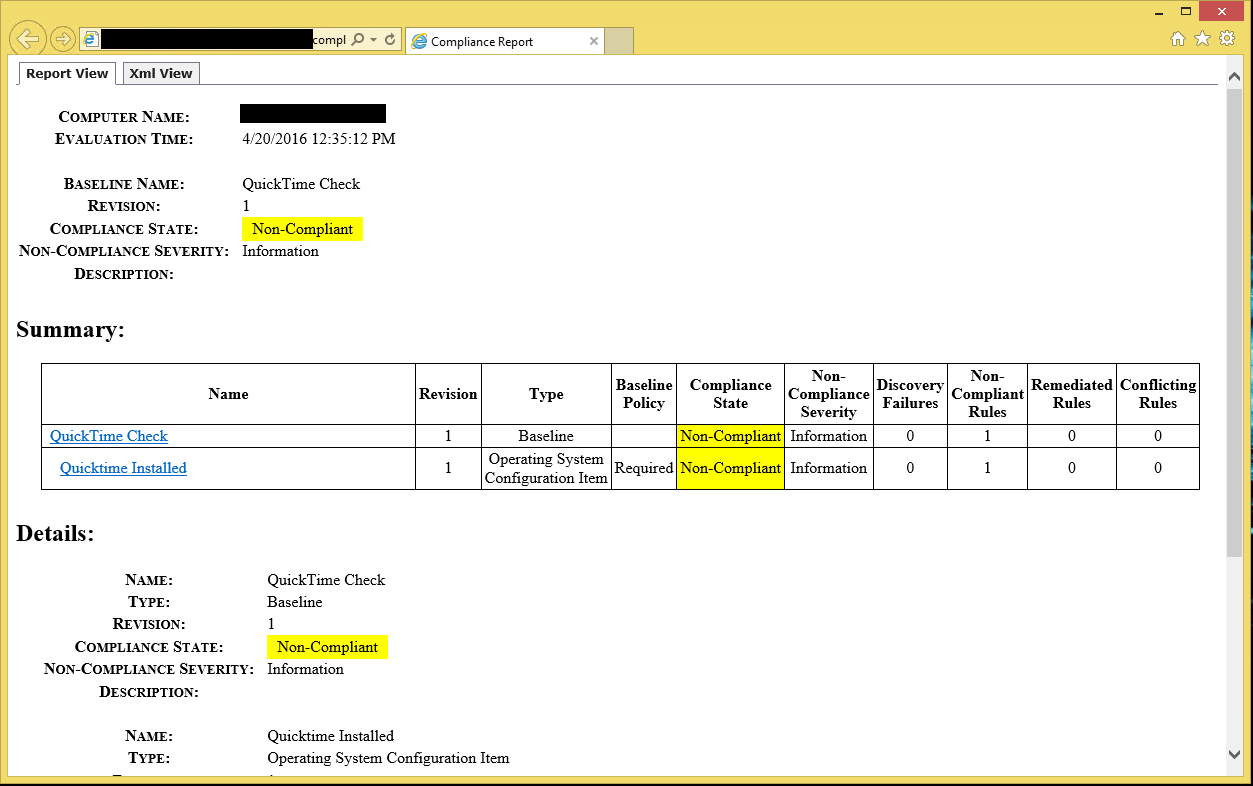
This computer will be a member of the Collection we created and receive the uninstall command. Once that is done, the next time the machine evaluates its compliance, it will see that it is now Complaint and will automatically remove it from that Collection. As time goes on, you will see the number of Non-Compliant computers diminish in the Collection. If anyone in your organization installs QuickTime in the future without your permission, you can rest easy knowing it will be uninstalled as soon as that computer evaluates itself.
This methodology can be used to remove any unwanted or risky software from your network. If you are interested in learning more about what SCCM can do, contact Arraya and schedule a demo today!
